Wednesday, December 26, 2007
USAID Partners with Microsoft to Unleash Lanka’s ‘Unlimited Potential’ in IT
Colombo, 22 November, (Asiantribune.com): The U.S. Agency for International Development (USAID) is partnering with Microsoft to introduce a new training curriculum developed with the assistance of the American information technology giant for four key sectors of the Sri Lankan economy.
USAID and Microsoft are co-financing the $236,000 project, which will be implemented by InfoShare, a nonprofit firm that develops IT solutions to nonprofit development organizations. Microsoft specially tailored the worldwide curriculum, known as Unlimited Potential, to boost Sri Lanka’s agricultural, apparel, tourism, and media/journalism sectors using IT.
“The forging of such public private partnerships is a cornerstone of USAID’s program here,” said USAID/Sri Lanka Mission Director Rebecca Cohn. “USAID’s goal of working toward a more prosperous and peaceful Sri Lanka cannot be achieved without the support and collaboration with partners dedicated to improving the skills and employability of youth.” USAID Mission Director Rebecca Cohn (left) and Microsoft’s Sriyan de Silva Wijeyeratne sign an agreement to finance a program that will boost IT skills in four key sectors of the Sri Lankan economy. (Photo: USAID/Zack Taylor)
USAID Mission Director Rebecca Cohn (left) and Microsoft’s Sriyan de Silva Wijeyeratne sign an agreement to finance a program that will boost IT skills in four key sectors of the Sri Lankan economy. (Photo: USAID/Zack Taylor)
The ambitious program will train at least 11,000 people, and provide scholarships to 2,000 needy students, many in the North-Central and Eastern provinces, Ms. Cohn said. In partnership with Microsoft, InfoShare has already begun to train about 110 instructors to teach the courses, which will be offered through various training organizations under the auspices of the Vocational Training Authority and private sector institutions.
“So much has happened in the area of information technology in the region with tremendously positive results,” said Sriyan de Silva Wijeyeratne of Microsoft. “We want to take on a bigger role in helping Sri Lanka access a bigger piece of this extremely beneficial pie.”
Ms. Cohn added that Unlimited Potential represents an important step to ensure Sri Lankan firms become and remain competitive in the international marketplace by ensuring that the workforce has the necessary skills in information technology.
“Modern information and communications technologies provide some enormously powerful tools for small and medium-sized businesses,” said Anuruddha Edirisinghe of InfoShare. “This IT curriculum, tailored to the needs of the four industries, will help them realize the full potential of their workforce and at the same time increase the employability of rural youth.”
The program targets some of its services to the East and North Central provinces, where there is a compelling need to retrain and reintegrate youth who have been previously involved in activities associated with the conflict.
The program is supported in part by the USAID Global Development Alliance (GDA), which supports private-public partnerships to serve as a catalyst to mobilize the ideas, efforts, and resources of the public sector, corporate America and non-governmental organizations in support of shared objectives. “USAID will continue to use the GDA model as an important part of its development strategy in Sri Lanka,” Ms. Cohn said.
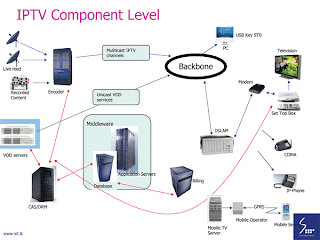
IPTV- Sri Lanka
Think of sitting in front of the TV and getting a more interactive session without just watching what's on but being able to watch the programmes you want, at the time you want, and getting a message on the screen alerting you of any phone call or SMS.
This may sound like something from the future, but this is coming to Sri Lanka and will be here next year come February.
Sri Lanka Telecom, the leading national telecom service provider is provide to giving the consumers with the latest in television technology with IPTV. The emerging technology that enables the delivery of broadcast quality TV and on-demand entertainment services over IP networks.
Broadcasting delivery will be carried out over an ADSL line by SLT that will be providing TV services becoming the clear competitor for the satellite TV networks already in Sri Lanka.
Services will include an over and above what the cable TV providers already have with the introduction of interactive services, Voice on Demand, time-shifted TV.
The main target will be residential market providing delivery on TV with interactive , SLT's ISP Services Head of Section Irshad Deen said.
He noted that the content will include broadcast TV with sports, entertainment and light, educational and serious niche segment as well.
"This will be a paradigm shift and a giant convergence step from telco to broadcasting communication," he said.
The biggest part is the when and how way in which the customer wants to watch the TV because of interactivity it helps to bring services to be more interactive-based.
"We are in the process of selecting the right platform with a set up Master Control Room to ensure right quality," Deen explained.
Security will also be protected heavily with water marking with AES algorithm which is able to protect the content over the network, he said.
Initially SLT will be providing voice via telephone or mobile, data on broadband internet access and video through television allowing the customer to have the full use of triple play. But quadruple play which will involve all of these services along with wireless service provisions will allow customers sometime later be able to access these services while on the move.
From senior citizens to the hip youth and kids, services will be made available with Cartoon TV, video games, handset games, music download, ring tone downloads, mobile video games, news, music and radio, TV and movies, sports news will involve the focus services.
A convergence of services via one network will be the best deal that will be up on offer through this new technological advancement that will hit Colombo initially and later go to the regions next year.
This service will prove to be a win-win solution for all with an estimated US$25 billion CAPEX for IPTV related infrastructure and content by 2010 which aptly applies for vendors of this service.
Broadcasters will be able to deal with professional telco organizations, have accountability of viewer-ship, ability to offer enhanced services and increase revenue; while operators will be able to access new revenue streams, reduced churn and obtain higher valuation for wire line.
Customers will have a wider choice of reliable and accountable service providers, digital quality programming and flexibility of subscription packages in addition to new services such as interactivity, gaming, video call and VoD.
IPTV- Sri Lanka
Think of sitting in front of the TV and getting a more interactive session without just watching what's on but being able to watch the programmes you want, at the time you want, and getting a message on the screen alerting you of any phone call or SMS.
This may sound like something from the future, but this is coming to Sri Lanka and will be here next year come February.
Sri Lanka Telecom, the leading national telecom service provider is provide to giving the consumers with the latest in television technology with IPTV. The emerging technology that enables the delivery of broadcast quality TV and on-demand entertainment services over IP networks.
Broadcasting delivery will be carried out over an ADSL line by SLT that will be providing TV services becoming the clear competitor for the satellite TV networks already in Sri Lanka.
Services will include an over and above what the cable TV providers already have with the introduction of interactive services, Voice on Demand, time-shifted TV.
The main target will be residential market providing delivery on TV with interactive , SLT's ISP Services Head of Section Irshad Deen said.
He noted that the content will include broadcast TV with sports, entertainment and light, educational and serious niche segment as well.
"This will be a paradigm shift and a giant convergence step from telco to broadcasting communication," he said.
The biggest part is the when and how way in which the customer wants to watch the TV because of interactivity it helps to bring services to be more interactive-based.
"We are in the process of selecting the right platform with a set up Master Control Room to ensure right quality," Deen explained.
Security will also be protected heavily with water marking with AES algorithm which is able to protect the content over the network, he said.
Initially SLT will be providing voice via telephone or mobile, data on broadband internet access and video through television allowing the customer to have the full use of triple play. But quadruple play which will involve all of these services along with wireless service provisions will allow customers sometime later be able to access these services while on the move.
From senior citizens to the hip youth and kids, services will be made available with Cartoon TV, video games, handset games, music download, ring tone downloads, mobile video games, news, music and radio, TV and movies, sports news will involve the focus services.
A convergence of services via one network will be the best deal that will be up on offer through this new technological advancement that will hit Colombo initially and later go to the regions next year.
This service will prove to be a win-win solution for all with an estimated US$25 billion CAPEX for IPTV related infrastructure and content by 2010 which aptly applies for vendors of this service.
Broadcasters will be able to deal with professional telco organizations, have accountability of viewer-ship, ability to offer enhanced services and increase revenue; while operators will be able to access new revenue streams, reduced churn and obtain higher valuation for wire line.
Customers will have a wider choice of reliable and accountable service providers, digital quality programming and flexibility of subscription packages in addition to new services such as interactivity, gaming, video call and VoD.
To all Sri Lankan on working late.
views on staying late in the office
Dear All,
It's half past 8 in the office but the lights are still on...
PCs still running, coffee machines still buzzing...
and who's at work? Most of them??? Take a closer look...
All or most specimens are ??-something male species of the human
race...
Look closer... again all or most of them are bachelors...
and why are they sitting late? Working hard? No way!!!
Any guesses???
Let's ask one of them...
Here's what he says... "What's there 2 do after going home... here we
get to surf, AC, phone, food, coffee.. that is why I am working late...
importantly no bossssssss!!!!!!!!!!!
This is the scene in most research centers and software companies , and
other off-shore offices.
Bachelors "time-passing" during late hours in the office just bcoz they
say they've nothing else to do...
Now what r the consequences... read on...
"Working"(for the record only) late hours soon becomes part of the
institute or company culture.
With bosses more than eager to provide support to those "working" late
in the form of taxi vouchers, food vouchers and of course good
feedback,(oh, he's a hard worker... goes home only to change..!!).They aren't helping things too... To hell with bosses who don't understand the difference between "sitting" late and "working" late!!!
Very soon, the boss start expecting all employees to put in extra
working hours.
So, My dear Bachelors let me tell you, life changes when u get married
and start having a family... office is no longer a priority, family is...
and that's when the problem starts... becoz u start having commitments at
home too.
For your boss, the earlier "hardworking" guy suddenly seems to become a
"early leaver" even if u leave an hour after regulartime... after doing
the same amount of work.
People leaving on time after doing their tasks for the day are labeled
as work-shirkers...
Girls who thankfully always (its changing nowadays... though) leave on
time are labeled as "not up to it". All the while, the bachelors pat their
own backs and carry on "working" not realizing that they r spoiling the
work culture at their own place and never realize that they wuld have to
regret at one point of time.
* So what's the moral of the story?? *
* Very clear, LEAVE ON TIME !!!
* Never put in extra time " *unless really needed *"
* Don't stay back un-necessarily and spoil your company work culture
which will in turn cause inconvenience to you and your colleagues.
There are hundred other things to do in the evening..
Learn music...
Learn a foreign language...
try a sport... TT, cricket.........
importantly Get a girl friend or gal friend, take him/her around
town...
* And for heaven's sake net cafe rates have dropped to an all-time low
(plus, no fire-walls) and try cooking for a change.
Take a tip from the Smirnoff ad: *"Life's calling, where are you??"*
Please pass on this message to all those colleagues And please do it
before leaving time, don't stay back till midnight to forward this!!!
ITS A TYPICAL SRILANKAN MENTALITY THAT WORKING FOR LONG HOURS MEANS VERY HARD WORKING & 100% COMMITMENT ETC.
PEOPLE WHO REGULARLY SIT LATE IN THE OFFICE DON'T KNOW TO MANAGE THEIR TIME.
SIMPLE !!!
LTTE a trend setter in cyber terrorism
Colombo, 29 October, (Asiantribune.com): This month marks 20 years since the Indian Peace Keeping Force launched 'Operation Pawan' against the Tigers in response to their mortar and machine gun attacks on IPKF patrols. The only photo-journalist present in the combat zone at the height of the battle for Jaffna was India Today'sShyam Tekwani. Having been taken to Jaffna , by the LTTE, he was witness to actual battle scenes and obtained a unique insight to Tiger tactics, their weapons, morale and mentality. His cover story appeared in the India Today of November 15, 1987 under the title, ' Sri Lanka: A Bloodied Accord' with a picture of an Indian soldier killed by the LTTE in Kokuvil.
Now, two decades later with a wealth of experience with the Tigers behind him he draws attention to lessons that all governments fighting the terrorist menace had better learn if they are to effectively meet the challenge.
Presently Assistant Professor, School of Communication and Information, Nanyang Technological University, Singapore, Tekwani's exclusive reportage of the conflict has been published internationally.
Addressing the recently concluded International Conference on Countering Terrorism in Colombo, he said:
"To understand the significance of the regional security threat posed by the LTTE it is necessary first to examine the relationship between terrorism and new media technologies. The information revolution in Asia offers terrorist groups the same benefits and advantages that it extends to business enterprises in the region.
Increased globalization and rapid absorption of new media technologies into business practices has enabled the ongoing dynamic economic environment in many Asian nations. Just as business corporations in Asia are adapting their tactical and operational strategies to make the best use of new technology and the emerging global economy, extremist groups are doing the same." Tekwani was speaking on 'The LTTE's online network and its implications for Regional Security.'
Tekwani recalled that the IPKF lost the media war against the Tigers having failed to win the confidence of journalists. It clearly proved the theory that terrorists understand the value of the media far better than governments.
He recalled that once when he returned from the battle zone after seven weeks he was amazed to read in the Indian press reports that were almost a total distortion of the real situation. He did not require much intelligence to realize that the LTTE had fed these newspapers with virtually fabricated stories.
"The LTTE branded the IPKF the 'Indian People Killing Force' and – sometimes – the 'Italian-Parsi Killing Force.' The latter was meant to personally ridicule Sonia (Italian) and Rajiv Gandhi (Parsi)."
Tekwani said that the Western media too had eagerly lapped up everything that the Tigers offered to them, since the former always loves any group that projects itself as the underdog, although the today the world is beginning to see the LTTE as an integral part of the international terrorist network.
"The Tigers are so clever in deceiving the young that when I show my students Tiger websites meant for different audiences the students are impressed and almost express support for the LTTE cause. But afterwards when I explain to them the organization's background and who the Tigers really are they begin to think differently."
He observed that one of the main factors affecting the Sri Lankan military's handling of the LTTE has been dwindling morale, whittled away by the support the LTTE had garnered in its early years from the international community. This was in large part due to its international propaganda campaign, which capitalized on its status as a marginalized minority and used the propaganda to focus on the sufferings of the Tamils rather than the violence of its own actions.
"The LTTE continues to do so with considerable success on the Internet."
In addition, Tekwani says, the LTTE has also ventured into cyber crime on occasion. He recalled that the Tigers had used the Internet to hack into Sri Lankan Government networks in 1997 - the first recorded use of Internet in the world by any conventional terrorist group. The Tigers are also reported to have used the Internet for criminal profit, as evidenced by the University of Sheffield case, which exposes the more serious issue of the Internet identity theft by terrorists.
According to him, the Tigers were also able to hack into the Sheffield University in England in 1997, and use the university computer system to send their propaganda and to engage in fund raising. And they did it in a covert manner. Having captured legitimate user IDs and passwords of well-respected university academics to disseminate e-mail communications around the world, they used those legitimate e-mail accounts and asked people to send money to a charity in Sri Lanka! While such instances are not yet the norm, they are undeniably the trend of the future. And the LTTE is nothing if not a trend setter in such tactics.
Tekwani regretted that the Sri Lankan Government - which many perceive as having lost the propaganda war with the LTTE even more thoroughly than it has the war on the ground – has no infrastructure legal or technical, to block access to LTTE and pro-LTTE sites within Sri Lanka even though the State has its own press, radio and television.
"This is a loop hole the LTTE has used well. In a related matter the creator of the 'I Love You' virus in the Philippines escaped punishment because the government there had no laws in place to prosecute cyber crimes. The situation is depressingly similar across Asia with the exception of perhaps Singapore. Asian nations are getting on to the information highway without any traffic laws in place…"
Tekwani noted that the LTTE was one of the first groups to use the Internet in its campaigns. The LTTE's use of the Internet and other new media and communication technologies as an integral part of its campaign represents an emerging security issue in the region, according to him.Sri Lanka ranks no.2 of the software piracy in Asia
Colombo, 24 October, (Asiantribune.com): The software piracy rate of Sri Lanka is the second to Bangladesh which ranks 92% .At present Sri Lanka ranks 90 % , according to a recent Global software Piracy Report conducted by the IDC- a global research and forecasting firm , said Roland Chan , Director of the Business Software Alliance of Singapore [BSA].
Speaking at a press briefing held in this morning in Colombo he said due to the software piracy the software industry losses over 86 million US$ per annum.
Replying questions of the reporters, he said this means that nine out of ten software installed personal computers in 2006 in Sri Lanka was unlicensed or obtained illegally through software theft.
The findings of the study have highlighted the need for action against software piracy in Sri Lanka, where it has taken a heavy toll on personal and business users as well as overall economy. The broader economic impact of software piracy is significantly greater than the retail value of pirated software, he said.
Among the many negative consequences of software piracy is the crippling of local software industries because of competition with pirated software, lost tax revenues and jobs from the lack of a legitimate market and decreased business productivity from using unsupported and unwarranted software.
Stemming the tide of piracy in Sri Lanka can only be achieved through industry education and awareness and proactive government led enforcement efforts . Software piracy is tantamount to software theft and therefore forbidden by the law of Sri Lanka . He commended local law imposing agencies and said Sri Lanka has already passed a number of bills to end computer crime and protect Intellectual Property Rights of the entrepreneurs.
Replying queries made by the media, the BSA Director explained the risks of using pirated software are vast-there is no warranty or support and users may even run the risk of fraud and identity theft.
He said the BSA which was formed in 1988 is making a concerted effort through software asset management to raise awareness about software piracy.
BPO in the A’pura backwoods
 |
| OnTime operators |
MAHAVILACHCHIYA, Anuradhapura - Business Processing Outsourcing (BPO) is a growing business globally which Sri Lanka has now cottoned onto quite capably.
Dozens of BPO’s are springing up here as global companies look for cost effective ways of handling their back-office operations in countries where labour and communications are cheaper than the west.
Yet ever heard of a BPO company in a jungle setting, next to a wild life park and subject to the occasional threat by the LTTE? OnTime Pvt Ltd is part of rural Sri Lanka’s first IT village, Horizon Lanka in the backwoods of Mahavilachchiya (adjoining Wilpattu) off Anuradhapura, where a group of youth processes data for a fee.
There is nothing different in the BPO industry in processing information inside the office of the client or the service provider located elsewhere. For example, staff at Mahavilachchiya’s proud company, OnTime, processing marketing data for a John Keells Group subsidiary daily could – if we close the curtains in this nice office surrounded by shady trees and occasional bird calls – very well be inside a JKH office in Colombo. There’s nothing different.
OnTime operators log into a JKH SAP accounting system through a secured link and enter data like prices and quality of suppliers. Some 150 documents are handled by one operator per day. Dialog Telekom and Singer are expected to join OnTime as its next clients with negotiations going on with the two parties.
“The BPO entry came as we needed to create job opportunities for our youngsters to remain in the village after their initial learning in English and IT,” said Nandasiri Wanninayaka (better known as ‘Wanni”), the village boy-English teacher-turned village entrepreneur.
Horizon Lanka, Sri Lanka’s first IT village, is a revelation itself. Launched by Wanni, as a Mahavilachchiya school teacher, in 1998, the initiative began as an English teaching exercise for the children whose parents were mostly rice farmers. From there with one computer donated by the US embassy, impressed by an English journal that the students did, the village has progressed to a centre of IT learning where one in every eight families has a computer (a ratio of 100 computers for 800 families).
Unheard of before but in these backwoods poor farmers are reading online newspapers in the comfort of their makeshift homes with uptodate computers with the help – unbelievable again – of seven wifi zones under a new technology called MESH. Here a section of the village amidst paddy fields and streams has wireless Internet access at all times.
Wanni and his Horizon Lanka exploits are legendary and profiled in newspapers and TV stations across the world. The IT village’s biggest opportunity probably came when Wanni and his best students shared the stage with Intel Chairman Dr. Craig Barrett in December 2005, during the latter’s visit to Sri Lanka and presence at a major IT conference.
The idea of setting up a BPO emerged as Wanni pondered on the next level of development. “Having taught English and then IT, the next issue was where do they get jobs? How can we retain them in the village?” he asked.
Enter the Foundation for Advancing Rural Opportunities in Sri Lanka (FAROLanka) to help Horizon set up its BPO and find its first client. FARO’s help however comes with some conditions – Wanni’s support and guidance to help other villages to develop on similar lines which the latter and his team are more than willing to do.
Isuru Senevirathna is OnTime’s Operations Director. He has received BPO training – along with another OnTime employee – in Laos and India sponsored by John Keells.
The 20-year old youth like any other Mahavilachchiya youngster would have had to either join the armed forces (in the case of girls it’s garment factories) or remain in the village as a farmer, until Wanni and his vision came along. Now Isuru is the proud owner of a motor cycle, happy and contended.
OnTime CEO is Nirosh Manjula Ranathunga, a 30 year-old graduate from Kelaniya University who studied IT while doing his B.Com degree. Ranathunga, who lives in Anuradhapura and visits Horizon twice a week saying he can handle operations from his home town easily through email/Internet, is also interested in transferring his skills and learning to other villages. He has his own company, Real Business Solutions, and runs a formerly-owned Horizon Lanka cyber café in Anuradhapura.
“I joined Horizon Lanka two years ago as a project manager and I’am very happy with this BPO initiative,” he said. Some 50 youths are being trained to take up BPO jobs in Mahavilachchiya which has a modern computer lab with 512 KBPS Internet connection. The Horizon Lanka website is www.horizonlanka.org
Code Smart: Solution to classpath too long (aka input line too long) problem in Windows
If you use Java in Windows, you're bound to run into classpath too long problem when your classpath grows. Windows has a limit (1KB - 2KB) of characters you can have on one single command line. The infamous "Input line is too long" is very annoying. Here's a trick to get around it.
"java.exe" command also scan for classes from the environment variable "CLASSPATH". If you can break your classpath into separate folders and jars, you can concatenate them like this:
setlocal
set CLASSPATH=c:/my/first/jar/somejar.jar;%CLASSPATH%
set CLASSPATH=c:/my/second/jar/someotherjar.jar;%CLASSPATH%
set CLASSPATH=c:/path/to/a/folder;%CLASSPATH%
.......
.......
java com.mycompany.Main
endlocal
By using CLASSPATH env variable, you don't need to pass it in to "java" command. The setlocal/endlocal pair ensures the CLASSPATH is "local" to this process and won't pollute the systemwise value.
--------
Updated:
Travis has pointed out that there is a limit on environment variable in Windows. I found it limited to 8K. So this isn't an absolute solution but it should sustain you for awhile. As suggested by D, you could shorten the path by using virtual drive. Further more, JDK6 has supported wildcard (*) in classpath.
Virtual drive:
Say you have bunch of jars under c:/path/to/lib
subst z: c:/my/path/to/lib
set CLASSPATH=z:/jar1.jar:%CLASSPATH%
Or with JDK6:
set CLASSPATH=c:/path/to/lib/*:%CLASSPATH%
Success of Google - Running the business in Buddhist way
Google was not started by a businessman with mere profit in mind, but it began as a research project in January, 1996 by Larry Page and Sergey Brin, two Ph.D. students at Stanford University, California. They hypothesized that a search engine that analyzed the relationships between websites would produce better results than existing techniques. So they turn their idea into a business.
Democracy on the web works.
While other search engines like Yahoo was making money by both URL submit and search facility, Google never intended to make money from web site owners to get them undue preference in searching in return for their paying. Google identified that this will result in poor search experience for web search users. Google assesses the importance of every web page using a variety of techniques, including its patented PageRank™ algorithm which analyzes which sites have been "voted" the best sources of information by other pages across the web.
Simplicity is the power
The start starter/home page for the Google is one of the simplest web pages in the net. Ordinary people expect that when a company or person is growing, there need to be increase complexity. However, it's amazing that Google keeping its simplest form in google search and they have adapted the same approach in products like GMail, Google Talk, etc as well.
Google's services are run on several server farms, each consisting of thousands of low-cost commodity computers running stripped-down versions of Linux which is contrary to traditional tend of using big super processor mainframes. So success of google search is based on power of large number of small processors than having big super processor.
You can make money without doing evil
Google is a business. The revenue the company generates is derived from offering its search technology to companies and from the sale of advertising displayed on Google and on other sites across the web. However, you may have never seen an ad on Google. That's because Google does not allow ads to be displayed on their results pages unless they're relevant to the results page on which they're shown. So, only certain searches produce sponsored links above or to the right of the results. Google firmly believes that ads can provide useful information if, and only if, they are relevant to what you wish to find.
Not flashy and hindrance to the user
Google has also proven that advertising can be effective without being flashy. Google does not accept pop-up advertising, which interferes with your ability to see the content you've requested.
Trustworthy and reliable
Advertising on Google is always clearly identified as a "Sponsored Link." It is a core value for Google that there be no compromising of the integrity of our results. Google never manipulate rankings to put our partners higher in our search results. No one can buy better PageRank. Therefore users trust Google's objectivity and no short-term gain could ever justify breaching that trust.
Pleasant working experience
One of Googles key philosophy for employment is that "Work and play are not mutually exclusive".
Every Google engineer is encouraged to spend 20 percent (20%) of their work time on projects that interest them. Some of Google's newer services, such as Gmail, Google News and orkut, originated from these independent endeavors.
Promoting Open Source
Google has recently formed a partnership with Sun Microsystems to help share and distribute each other's technologies. As part of the partnership Google will hire employees to help the open source office program openoffice.org.
Google Code and Google Docs are two of the main project aiming toward free and open source culture.
If you're respectful by habit,Ref:
constantly honoring the worthy,
four things increase:
long life, beauty,
happiness, strength.
- The Buddha (Dammapada)
http://www.google.com/corporate/tenthings.html
http://www.google.com/support/jobs/bin/static.py?page=about.html&about
Wednesday, October 03, 2007
Programming Can Ruin Your Life
There are many essays and articles extolling the virtues of becoming a great programmer. You’ll have a sharp mind, great abstract reasoning skills, and a chance to become wealthy by working mere hours a day. This is what you’ve heard, right?
Sadly, no one ever tells you about the ways in which it will adversely affect your life. The physical effects are obvious. You’ll spend most of your time sitting, probably in an uncomfortable chair that doesn’t promote good posture. You’ll fuel yourself with food that is readily available, meaning it’s more than likely processed and full of sugar and you’ll likely choose either coffee or soda to stave off the drowsiness. A coworker once remarked, “If it doesn’t come out of a vending machine, programmers don’t eat it.”
But I’m not particularly interested in the health risks, as I said, they’re obvious. So what am I talking about? Programming changes more than your body. Programming changes the way you think. You might hear a programmer say, “I like python because it matches the way I think.” Or is it really that they’ve learned to think in python? Regardless of the language employed, you think differently when you program. No decent programmer will deny that. This is why it’s often so hard to explain to someone “how you do that” because, as clear as your explanation may be, you simply think differently. It is this change in thinking that can ruin your life.
The application of programming specific processes and habits to the everyday is where peril lies. The same traits that make you a great programmer can make you an awkward, misunderstood and miserable human being.
Programming presents you with a problem and allows you to eventually solve it provided you don’t quit. A solution is out there somewhere. Make enough attempts and chances are you’ll eventually prevail. Aren’t computers great? They afford a large degree of freedom in problem solving. If nothing else, you are able to make as may attempts as you please and it will happily execute each one. This instills in you a sense that failure is not final. Any obstacle can be hurdled. This is not true in the real world. While you may find second chances now and again, the wheels that turn in the big blue room are largely unforgiving. Time marches on in one direction.
When faced with an interesting programming problem your mind will chew it over in the background. Maybe it’s an algorithm you need to develop, maybe it’s a tricky architecture problem, maybe it’s data that needs to be modeled. It doesn’t matter. Your mind will quietly work the problem over in search of a solution. The “ah-ha!” moment will come when you’re in the shower, or playing Tetris. This practice of constant churning will slowly work its way into the rest of your life. Each problem or puzzle you encounter will start it’s own thread; the toughest and most troubling of which will be blocking.
A program is highly malleable. You can make a nearly unlimited number of changes. You can re-implement. You can optimize. You can run the compile-test-debug cycle ad infinitum. Make a change, see a result. Life is not like this. Every action you take is followed by a commit and the transaction cannot be rolled back. You can continue to make changes and optimizations as you move forward but the effects of these will not be immediately apparent. The instant feedback of development is sorely lacking in real life. Furthermore, your changes might simply be ignored. Data will be skipped. Blocks will not be executed. Optimizations will go unnoticed. The world is resistant to your tinkering.
Programmers become obsessed with perfection. This is why they are constantly talking about rewrites. They cannot resist optimum solutions. Perfection requires tossing aside mediocre ideas in search of great ones. A good programmer would rather leave a problem temporarily unsolved than solve it poorly. A good solution takes into account all predictable outcomes and solves the largest number of them in the most efficient way. This mindset prevents you from writing code with limited utility and life span. While it’s a wonderful trait to have in programming, the demons of scope and efficiency will start to assert themselves on your ordinary life. You will avoid taking care of simple things because the solution is inelegant or simply feels wrong. Time to think will no doubt yield a better result, you’ll say.
The obsession with perfection develops a forward-thinking mindset. The ability to anticipate provides a huge advantage because you won’t waist your time implementing solutions that ultimately fail due to short-sightedness or lack of imagination. You will constantly be mapping out flows and running the permutations through your head. Back in the real world, you will find yourself piecing together plans of breath-taking size and beauty that simultaneously resolve multiple problems and fulfill numerous dreams. You will attempt to kill every bird with one stone. The impossibility of actualizing these plans will be agonizing, yet your mind will continue to pour over every detail as it seeks to anticipate every possible outcome and construct the perfect solution.
Everything is now data. Every bit is worthy of attention. Every interaction is worthy of analysis. Your mind has been trained to do this since it is usually the insignificant or subtle bits that have to be rooted out when debugging. You will find it frustrating that everyone else does not collect and analyze data. You will notice details that others simply gloss over. Your penchant for detail and over-analysis will earn you strange glances and confused shrugs. Your decision making process will resemble that of your peers less and less.
The frantic pace of the software world will instill in you a sense of panic and urgency. You must do everything now. Tomorrow is too late. The thought of working constantly will no longer seem foreign or ridiculous. You will spend your free time feeling guilty about not working. But you will be working. Your hands may not be at the keyboard, but your mind will be.
The romanticized story of young upstarts toiling away in a garage to build the world’s next great company is alluring. It’s easy to convince yourself that the dream is there for the taking. But understand that there are many factors you cannot control. Luck and timing being but two. Don’t miss the life you have in the search for the one you think you want. To quote John Lennon, “Life is what happens while you are busy making other plans.” But perhaps Pascal said it best, “We never keep to the present. We … anticipate the future as if we found it too slow in coming and were trying to hurry it up, or we recall the past as if to stay its too rapid flight. We are so unwise that we wander about in times that do not belong to us and do not think of the only one that does; so vain that we dream of times that are not and blindly flee the only one that is… [We] think of how we are going to arrange things over which we have no control for a time we can never be sure of reaching… Thus we never actually live, but hope to live, and since we are always planning how to be happy, it is inevitable that we should never be so.”
Is programming the road to ruin? Or is it that those with a predilection for detail and mental gymnastics find themselves drawn to it. Perhaps it simply exacerbates a pre-existing mindset. There are certainly other traits (stereotypical or not) that most programmers seem to share. I have focused mainly on the negative impacts, but there are certainly positive ones as well. All things listed as bad can be good if simply kept in check. Obsession is dangerous, and anything great requires obsession. Programming is no exception.
Single Sign On
SSO is by no means a new technology. It has been in use for a long time. Even before the Web Applications were available.
The most primitive of SSO systems is a piece of paper per user with a small table listing systems with the user names and passwords. This list can be generally stamped on the user monitor. Later on it can evolve, instead any simple piece of paper, it can be a post-it.

(for those of you interested in how I created this picture, I did it using the napkin look and feel)
Yes, you might be thinking that I am kidding here. And to some extent I am. However, this has been a big concern in the corporate world. That's the way it used to be, not by design, and it still is in some companies. Lots of applications, managed by different teams in the famous "silos", not integrated, each requiring the user to authenticate with its own username/password... you know the picture.
I think that that's how the need of SSO got started.
Early SSO systems worked as the post-it that the users where sticking to their monitors.
They were repositories of users/passwords pairs protected by a password. In that way before the user would authenticate to the destination system, they would first access the SSO repository, fetch their passwords, and continue authenticating with the system they were intending to work on the first place.
Lately, In a web based environment, this can be extremely simplified with a well know device: cookies.
Example
We will go over an SSO implementation with an example. Let's have 3 major components: The SSO server, Application A, Application B.Here is how the system would work:
1) The user tries to access the application A.
2) Application A realizes that the user has not been authenticated. (See "user has been authenticated" for details).
3) Application A sends an HTTP redirect to the SSO server.
4) The SSO server sees that the user is not authenticated (again, See "user has been authenticated" for details).
5) The SSO server requires the user to authenticate.
6) The user submits username/password
7) SSO Server validates username/password. If they are valid, the user is "granted permission".
8) The user is redirected to Application A.
9) Application A sees that the user has been authenticated, and proceeds.
Granting permission:
When the username and password are validated by the SSO server, a unique large token is generated for the user. The token is going to have a unique identifier for the user's session. The SSO server keeps a list of the tokens associated with the credentials of the user that owns it. This token is set by the SSO server in the user's browser as a cookie.User has been authenticated:
For an application to validate that a user has been authenticated it has to follow this steps:1) Check for the token in the cookies.
2) Query the SSO server for the credentials associated with the token. If the token is valid, the SSO returns the credentials of the user for the application to continue. If the token is not present, or is invalid, the application knows that the user has not been authenticated, and is redirected to the SSO server.
This makes it look like there is a lot of work to get this type of setup. Luckily, it is not complicated at all. Most SSO servers come with a plug-in that is installed in the application/web server that intercepts all the requests, and performs the logic just described. Any application deployed in such a server will automatically get the user credentials, populated by the plug-in, just as if the user was authenticated locally using the JAAS framework.
A Note on Cookies
As most of you know the capabilities of setting and reading cookies are restricted by the domains. A web server that does not belong to the domain where the cookie was set will not be able to read the cookie.For that reason the applications and the SSO server have to belong to the same domain. Indeed, if they are not to be part of the same domain the cookies would not work. For that case the URL rewriting technique can be used.
Development TIP:
When you are developing your app, no need to authenticate with the SSO. Just have each developer to work with a simple JAAS authentication within a local flat file (most of the IDEs have this by default). Get them to complete the development, and when you are ready to test, deploy it in your testing environment using the SSO plugin.Napkin Look and Feel
Latest
New Wiki
Our Wiki gives you a place to share ideas and advice with other folks. We've started it off with some instructions about how to get Java applications to use Napkin for their Look and Feel.Latest Release: 1.0, 18 March, 2006
- Upgrade to Java 1.5.
- Several bugs vanished with this upgrade, but it does mean that this will not work anymore with earlier Java versions. So far it has seemed too much work to maintain a system that can work on both.
- Sketched icons added
- Peter Goodspeed and Justin Crafford created a cool package to take an XML description of an icon and randomly perturb it around. This lets us easily have icons for dialog boxes, for example, that look sketched and slightly different each time. This is in the subpackage net.sourceforge.napkinlaf.sketch, and you can use it for diagrams as well. It's really, really cool.
- Works on Windows
- Alex Lam took an interest in using Napkin as his default look & feel for NetBeans. Rather than refer him to an appropriate mental health professional, I put him on the team. He has fixed many, many issues, most specific to the Windows platform but including several other issues related to borders, opacity, and created a tileable sticky-note background for popups, etc. Welcome to the monkey house, Alex.
Overview
The Napkin Look & Feel is a pluggable Java look and feel that looks like it was scrawled on a napkin. You can use it to make provisional work actually look provisional, or just for fun.The idea is to try to develop a look and feel that can be used in Java applications that looks informal and provisional, yet be fully functional for development. Often when people see a GUI mock-up, or a complete GUI without full functionality, they assume that the code behind it is working. While this can be used to sleazy advantage, it can also convince people who ought to know better (like your managers) that you are already done when you have just barely begun, or when only parts are complete. No matter how much you speak to their rational side, the emotional response still says "Done!". Which after a while leads to a later question: "That was done months ago! What are they doing? Playing Quake?" A good article on this is Joel on Software's “The Iceberg Secret, Revealed”.
So the idea is to create a complete look and feel that can be used while the thing is not done which will convey an emotional message to match the rational one. As pieces of the work are done, the GUI for those pieces can be switched to use the "formal" (final) look and feel, allowing someone looking at demos over time to see the progress of the entire system reflected in the expression of the GUI.
Over time, several folks have just liked the thing and wanted to use it for non-provisional GUI's. Sometimes this is because the application itself seems to match the theme, such as a brainstorming tool. And sometimes it's just that it looks fun.
This is all done using the Java Swing pluggable Look & Feel framework.
Sightings
- Don't make the Demo look Done, from Kathy Sierra's blog Creating Passionate Users.
- "Finally, it's great to know that there are tools to help make the look match the state, with my favorite being the Napkin Look and Feel, a GUI "skin" for Java that makes the interface look -- quite literally -- like it was scrawled on a napkin."
- Matt Stephens' “Agile Development with ICONIX Process”
- "... if the working prototype was presented looking like a user interface mockup that had been scrawled on theback of a napkin, then the customer would be more likely to see it for what it actually is: a slightly working but mostly non-functional prototype... Seems like a great idea to us!" (You can read the pages here)
- NetBeans Look & Feel Competition
- Claudio Miranda submitted an entry with NapkinLAF on GTK.
- Kirill Grouchnikov's blog
- Compares various LAFs for their Right-to-Left menu alignment issues. Thanks to Kirill for reporting the issues ;-)
- BlogEd
- "I have added the napkin L&F to BlogEd and made it the default when run from cvs using 'ant run'. We can easily change it back if it gets in the way. The only bug I have noticed currently is that the pulling on the scrollbar seems to move the whole window. Perhaps Ken Arnold will know what the problem is there."
- Daniel Steinberg's blog at java.net, April 5, 2004
- A very nice & quick writeup.
- Front page note on javadesktop.org , April 1 2004
- Just a brief note pointing to the home page, but we got some good mail from it.
Acknowledgments
Peter Goodspeed and Justin Crafford created the sketching subsystem, as a senior project for their degrees at Worcester Polytechnic Institute. They did a great job, and solved an important problem. And thanks to Scott Anderson, a fellow student and friend of mine who suggested they get in touch with me to look for a thesis project.
Scott Violet of Sun has helped me pick apart some of the more abstruse and arcane bits of the plaf framework, which is full of 'em. Thanks a bunch, Scott, and thanks to Hans Muller, also of Sun, for plugging me together with him.
Brandon Franklin has contributed many spare cycles (of which he has none) to planning the upgrade to 1.5, making the whole process much easier.
The font "Felt Tip Roman" was created by Mark Simonson, who spent a lot of time with me on how to license this. He has kindly decided that this particular use does not require individual licensing for each user of the LAF, but can be done by special arrangement. The legalities are below, but beyond those legalities, we'd like to ask you all to be cool — if you like the font and want to use it, buy it properly. Making fonts is not easy, and font folks get their work ripped off far too often. If you do want to use it, buy it from his site http://www.ms-studio.com/, where he gets more from it.
The font "Ænigma Scrawl" was created by Brian Kent, and has worked very well for a handwritten font that scales reasonably to GUI-control sizes (most handwritten-style fonts are display fonts that only work in large sizes). To make things work better, Brian has adapted the font to adjust the spacing around some punctuation as well as some other tweaks. So the version released here is a custom one direct from the artist (which we believe he expects to roll back into the font at future date). We would like to thank Brian a lot for his quick and nimble cooperation, which made this work a lot better and easier on me.
Miro Jurišić has been very helpful in thinking through with me (sometimes for me) some of the hairy graphics problems. This definitely pushes into some poorly documented areas of the 2D API, and it has helped a lot to have someone to talk it through with. Thanks, Miro!
Brian Hawthorne created a quick and excellent selection of blueprint backgrounds for me to choose from. Thanks!
Several people have helped with testing, reporting bugs, and suggesting things. The most persistent have been: Deryl Steinert, Bob Herrmann, David Matuszek, Graham Perks, Henry Story, and Tom Eugelink. Thanks to all, and we'll be happy to have you be added to this list.
Essential firefox add-ons for web programmers
- FireFTP - is a free, secure, cross-platform FTP client for Mozilla Firefox which provides easy and intuitive access to FTP servers, FireFTP includes more advanced features such as: directory comparison, syncing directories while navigating, SSL encryption, search/filtering, integrity checks, remote editing, drag & drop, file hashing, and much more!
- IE Tab - is a great tool for web developers, since you can easily see how your web page displayed in IE with just one click and then switch back to Firefox.
- Firebug - integrates with Firefox to put a wealth of development tools at your fingertips while you browse. You can edit, debug, and monitor CSS, HTML, and JavaScript live in any web page.
- The Web Developer - adds a menu and a toolbar to the browser with various web developer tools.
- HTML Validator - is a Mozilla extension that adds HTML validation inside Firefox and Mozilla. The number of errors of a HTML page is seen on the form of an icon in the status bar when browsing.
- ColorZilla - you can get a color reading from any point in your browser, quickly adjust this color and paste it into another program. You can Zoom the page you are viewing and measure distances between any two points on the page. The built-in palette browser allows choosing colors from pre-defined color sets and saving the most used colors in custom palettes.
- CSS Validator - is a Mozilla Firefox extension which Validates a page using the W3C CSS Validator. Adds an option to the right-click context menu and to the Tools menu to allow for easy validation of the CSS of the current page.
- MeasureIt - draw a ruler across any webpage to check the width, height, or alignment of page elements in pixels.
- View formatted source - displays formatted and color-coded source and optional CSS information for each element.
- View Source Chart - draws a Color-Coded Chart of a Webpage's Source Code and displays Source in its Altered State After the DOM has been Manipulated by JavaScript.
- Venkman - the code name for Mozilla's JavaScript Debugger, aims to provide a powerful JavaScript debugging environment for Mozilla based browsers namely Firefox, Netscape 7.x/9.x series, Seamonkey 1.x/2.x.
- iWEBTOOL - Access over 30 Webmaster Tools for Free directly from your web browser
- http://livehttpheaders.mozdev.org/
- LinkChecker - check webpage links at a glance with simple color coding. Ditch those massive listings of bad links that provide no context and add LinkChecker to your arsenal of web development tools today.
- Load Time Analyzer is an extension created by Google that displays the number of events that are processed by a certain website and how long it takes to load them all. The load time displayed will obviously be influenced by your Internet connection, nonetheless it can provide a good indicator of the site speed.
- Quick Locale Switcher - Allows you to quickly change and apply a different locale (language) in your Mozilla application.
- XHTML-MP - allows firefox to render HTML content with the mime-type of application/vnd.wap.xhtml+xml. For any developer working with mobile applications, this provides an alternative to using a device emulator.
- Console² - let's you display errors filtered by type (Errors, Warnings, Messages), language (JavaScript, CSS, XML) and context (Chrome, Content). Furthermore it provides a simple search box (as seen in the History and Bookmarks sidebars), hiding of duplicates, sidebar optimizations, a customizable toolbar and some more accessibility improvements.
- Page validator - validates a page using the W3C Markup Validation Service. Adds an option to the right-click context menu and to the Tools menu to allow for easy validation of the current page. Opens the results in a new tab. This is a simple extension that will work only for online pages.
- xmldeveloper - helps XML developers with their programming efforts by supplying a central toolbar for everything XML.
- The Total Validator - provides one-click validation. Once installed all you do is browse to the page you want to validate then click on the 'TV' icon in the browser status bar.
- Modify Headers - allows the user to Add, Modify and Filter out HTTP request headers. See the help tab in the Modify Headers window for more information.
- The XPather - is a simple extension that integrates both with the browser and its DOMInspector. Thus, is't very lightweight and cross-platform. It is valuable mainly as a web/XML-app development and hacking tool.
- LiveHTTPHeaders - display http headers in real time while pages are being downloaded from the Internet
- Font Finder - Get all CSS styles of selected text in Firefox
Top 10+ source code search engines
Programmers are coding and coding in somewhere for some purpose. I wonder how many lines of code is written in a minute on the world :) I guess thousands of lines. But most them are coding the same snippets of code again and again. I always used "Koders" not to reinvent america, means not to rewrite the codes someone else have already solved. There are plenty of code search engines out there to serve us (programmers) with the millions of lines of codes to fasten our job. Here is the most used ones i could found on the internet.
- Koders.com - is the leading search engine for open source code. Our source code optimized search engine provides developers with an easy-to-use interface to search for source code examples and discover new open source projects which can be leveraged in their applications.

- O'Really Labs Code Search - The database currently contains over 123,000 individual examples, composed of 2.6 million lines of code — all edited and ready to use.
- Google /*Code Search*/ - is a free product from Google which debuted in Google Labs allowing web users to search for open-source code on the Internet. Features include the ability to search using operators. These are lang:, package:, license: and file:. The code available for searching is in various formats including tar.gz, .tar.bz2, .tar, and .zip, CVS and Subversion repositories as well as snippets from HTML pages such as Wikipedia itself.

- Codase - is an innovative and unique search engine for source code. Codase offers the best search results than any other services available today in source code search space.
- Krugle - is a search engine that allows programmers and other developers to search Open Source repositories in order to locate open source code, and quickly share the code with other programmers on the internet.
- JExamples - provides the ability to search for Java projects. The examples extracted from open source search engine understands the semantics of Java, so the search yields more accurate results than a text search. The site also provides the ability to rate examples so the highest rated examples will be shown first.
- JSourcery - Search open source Java APIs
- Merobase - is a software search engine that allows developers to find, share and reuse software components from the Internet. The engine harvests software components from a large variety of sources, including Apache, SourceForge, and Java.net.
- All The Code - is a source code search engine, presently for the Java language but with more languages being added soon. Unlike similar source code search engines, All The Code considers the relation between code and uses this to help judge the relevance.
- http://csourcesearch.net/
- EMC Dev Network - Searching 312,750 lines of code at EMC Developer Network. Powered by Kders.
- Codefetch - Its mission is to connect programmers and authors so that programmers get the information they need, and the work of authors is supported and encouraged.
- DevX's Sourcebank - is a directory of links to source code and script posted around the Web. Use the Search option to find terms within the source code. To cast the widest net, use the search with All Types selected. Or, you can browse through a subset of the code by categories (below). First, select a filter, such as C or Java, by clicking on one of the square buttons and then choose one of the categories (such as Mathematics) from within that filter.
Programming Handbooks and Cheatsheets
Cheat sheets are useful one page document which you should print out and post it on the wall from of your eyes. It helps you to learn the subject more quickly, and saves your time.
PHP- http://www.ilovejackdaniels.com/php_cheat_sheet.pdf
- http://www.blueshoes.org/en/developer/php_cheat_sheet
- Microsoft Ajax Library Cheat sheet
AJAX
CSS
- http://lesliefranke.com/files/reference/csscheatsheet.html
- http://home.tampabay.rr.com/bmerkey/cheatsheet.htm
- http://www.ilovejackdaniels.com/css/css-cheat-sheet
- http://home.tampabay.rr.com/bmerkey/cheatsheet.htm
- http://www.petefreitag.com/cheatsheets/css/
- http://refcards.com/download/bj/css2.pdf
- http://www.tek271.com/articles/css_cheat_sheet.html
Perl
- http://juerd.nl/site.plp/perlcheat
- http://www.regxlib.com/CheatSheet.htm
- http://search.cpan.org/~nwclark/perl-5.8.7/pod/perlcheat.pod
- http://www.mnlab.cs.depaul.edu/~ehab/Courses/TDC568/resources/PerlQuickRef.pdf
- http://heron.snell.clarkson.edu/it/perlrefcard.pdf
- http://johnbokma.com/perl/perl-quick-reference-card.html
- http://john-sheehan.com/blog/index.php/net-cheat-sheets/
- http://aspnetresources.com/downloads/ms_ajax_library_cheat_sheets1.zip
- http://www.yukoncollege.yk.ca/~ttopper/COMP118/rCheatSheet.html
- http://www-128.ibm.com/developerworks/library/l-cheatsheet3.html
- http://www.onlamp.com/python/excerpt/PythonPocketRef/examples/python.pdf
- http://www.drweb.de/weblog/weblog/?p=548
Javascript
Ruby on Rails
- http://ruby.cenophobie.com/RubyCheat.pdf
- http://www.blainekendall.com/uploads/RubyOnRails-Cheatsheet-BlaineKendall.pdf
- http://www.zenspider.com/Languages/Ruby/QuickRef.html
- http://www.threaded.com/ruby_cheatsheet.htm
- http://www.ilovejackdaniels.com/cheat-sheets/ruby-on-rails-cheat-sheet/
- http://slash7.com/cheats/rails_files_cheatsheet.pdf
- http://slash7.com/cheats/activerecord_cheatsheet.pdf
- http://railshandbook.com
- http://www.blainekendall.com/index.php/rubyonrailscheatsheet/
- http://www.rubyonrailsblog.com/articles/2006/10/04/ruby-on-rails-cheat-sheet-collectors-edition
Java
- http://mindprod.com/jgloss/jcheat.html
- http://lesliefranke.com/files/reference/javacheatsheet.pdf
- http://www.petefreitag.com/cheatsheets/java/
- http://whatis.techtarget.com/definition/0,,sid9_gci826135,00.html
- http://www.petefreitag.com/cheatsheets/java/
- http://www.janeg.ca/JQREF.pdf
JSP
- http://ndpsoftware.com/JSPXMLCheatSheet.html
- http://www.digilife.be/quickreferences/QRC/JSP%20Syntax.pdf
- http://java.sun.com/products/jsp/syntax/2.0/card20.pdf
Javascript
- http://tiger.la.asu.edu/Quick_Ref/javascript_cheat_sheet.pdf
- http://www.werelight.com/docs/JavaScript_Quick_Reference.htm
- http://www.ilovejackdaniels.com/javascript/javascript-cheat-sheet/
HTML
- http://www.webmonkey.com/webmonkey/reference/html_cheatsheet/
- http://lesliefranke.com/files/reference/htmlcheatsheet.pdf
- http://www.psacake.com/web/dy.asp
- http://cdburnerxp.se/htmlcheatsheet.pdf
- http://www.cookwood.com/html/extras/entities.html
- http://www.modularmedia.com/xhtml_standards/xhtmlcheatsheet.html
- http://www.petefreitag.com/cheatsheets/xhtml/
- http://www.angelfire.com/nm/thehtmlsource/html/cheatsheet.html
Unix
- http://mainline.brynmawr.edu/~gtowell/unix.pdf
- http://freeengineer.org/learnUNIXin10minutes.html
- http://www.rain.org/%7emkummel/unix.html
- http://www.pixelbeat.org/cmdline.html
Linux
C
C#
Django
- http://www.buayacorp.com/images/articulos/postgresql-cheat-sheet-big.png
- http://www.yagc.ndo.co.uk/cheatsheets/plsql_cheatsheet.html
- http://www.scottferguson.com/pages/SybaseSystem11SQLCheatSheet.pdf
- http://www.ilovejackdaniels.com/php/mysql-cheat-sheet/
- http://nparikh.freeshell.org/unix/mysql.php
- http://www.3gwt.net/demo/SQL_redux.html
- http://www.nparikh.org/unix/mysql.php
- http://www.vttoth.com/oracle.htm
Web Development
Others
Most popular free/open source IDEs and Editors
I'm getting acquainted with Wicket (which I blogged about here). In doing so, I encountered some problems and got a few responses from Wicket's mailing list. Someone suggested that I use Log4j to debug my issues, and so -- for the first time -- I used Log4j today. So here, as a reminder to myself and possibly of benefit to others, is what I did to use Log4j for debugging a Wicket application deployed over Tomcat from NetBeans IDE:
- Stop the running Tomcat instance. (In the IDE's Runtime window.)
- Download Commons Logging and copy the JAR to Tomcat's common/lib folder.
- Download Log4j and copy the JAR to Tomcat's common/lib folder.
- Create a log4j.properties file in Tomcat's common/classes folder. Make sure it contains the following line:
log4j.logger.wicket.util.resource=DEBUG
The above line is only for the resource package. To enable debugging for all the Wicket packages, use this instead:
log4j.logger.wicket=DEBUG
This is my log4j.properties file. Make sure that you change the log4j.appender.R.File property to point to logs/tomcat.log file in Tomcat's base directory (which is inside the NetBeans IDE user directory).
- Deploy the Wicket application. (In the IDE's Projects window.)
- Go to the logs/tomcat.log file in Tomcat's base directory and, if errors have been picked up, note that there are lines such as the following:
2005-07-02 20:41:25,140 [http-8084-Processor23]
DEBUG wicket.util.resource.locator.ResourceStreamLocator -
Attempting to locate resource 'wicket/examples/navomatic/Page1.html'
on path [folders = [\], webapppaths: []]
Finally, I've found this document to be very helpful in setting up Log4j for Tomcat: Logging for Apache Tomcat and Velocity using Log4j
Log4j, Wicket, Tomcat, and NetBeans IDE
I'm getting acquainted with Wicket (which I blogged about here). In doing so, I encountered some problems and got a few responses from Wicket's mailing list. Someone suggested that I use Log4j to debug my issues, and so -- for the first time -- I used Log4j today. So here, as a reminder to myself and possibly of benefit to others, is what I did to use Log4j for debugging a Wicket application deployed over Tomcat from NetBeans IDE:
- Stop the running Tomcat instance. (In the IDE's Runtime window.)
- Download Commons Logging and copy the JAR to Tomcat's common/lib folder.
- Download Log4j and copy the JAR to Tomcat's common/lib folder.
- Create a log4j.properties file in Tomcat's common/classes folder. Make sure it contains the following line:
log4j.logger.wicket.util.resource=DEBUG
The above line is only for the resource package. To enable debugging for all the Wicket packages, use this instead:
log4j.logger.wicket=DEBUG
This is my log4j.properties file. Make sure that you change the log4j.appender.R.File property to point to logs/tomcat.log file in Tomcat's base directory (which is inside the NetBeans IDE user directory).
- Deploy the Wicket application. (In the IDE's Projects window.)
- Go to the logs/tomcat.log file in Tomcat's base directory and, if errors have been picked up, note that there are lines such as the following:
2005-07-02 20:41:25,140 [http-8084-Processor23]
DEBUG wicket.util.resource.locator.ResourceStreamLocator -
Attempting to locate resource 'wicket/examples/navomatic/Page1.html'
on path [folders = [\], webapppaths: []]
Finally, I've found this document to be very helpful in setting up Log4j for Tomcat: Logging for Apache Tomcat and Velocity using Log4j
Friday, September 28, 2007
Hibernate dynamic mapping and Dom4J enabled sessions
Imagine that you have an application or an SDK which help users to manipulate data from different RDBMSs. Hibernate provide rich configuration facilities which help you configure Hibernate dynamically in term of adding mapping data or other configuration artifacts that usually stores in hibernate.cfg.xml or equal properties files.
As we are planning to use Hibernate dynamic mapping and Dom4J entity mode i am going to blog about it during my evaluation.
OK, Hibernate provide 3 kinds of entity mode
POJO
DOM4J
MAP
Default mode sets to be POJO as it is most commonly used mode. This modes tell session how it should handle entities. We can configure a session to use any of this modes when we need that mode, but we can configure it in hibernate configuration file for by adding a property like
As you can see it is a basic ant based project.
Let me give you content of each file and explain about it as much as i could. First of all lets see what we have in hibernate.cfg.xml
We have one mapping file which is named student.hbm.xml so we include it into the configuration file. If you do not have MySQL around then use Derby which is included into NetBeans ;-) .
Log4J configuration is another traditional one, as you see log4j.appender.stdout=org.apache.log4j.FileAppender log4j.appender.stdout.File=messages_dynamic.log log4j.appender.stdout.layout=org.apache.log4j.PatternLayout log4j.appender.stdout.layout.ConversionPattern=%d{ABSOLUTE} %5p %c{1}:%L - %m%n log4j.rootLogger=WARN, stdout
We used a file appender which send formatted log entry into a file named messages_dynamic.log in project root directory. next file which we are going to take a look is Student.hbm.xml it is our mapping file, where we define the student as a dynamic entity.
Next step is looking at our HibernateUtil which is known to the community for Hibernate booting and hibernate instance management.
here is its code:
package persistence;
import org.hibernate.*;
import org.hibernate.cfg.*;
public class HibernateUtil {
private static SessionFactory sessionFactory;
static {
try { sessionFactory = new Configuration().configure().buildSessionFactory(); }
catch (Throwable ex) { throw new ExceptionInInitializerError(ex); }
}
public static SessionFactory getSessionFactory() { return sessionFactory; }
public static void shutdown() { getSessionFactory().close(); }
}
Noting extra here. lets look at last part in which we try to use dom4j session to manipulate our data.
package dynamic;
import java.util.*;
import org.hibernate.EntityMode;
import org.hibernate.Query; import org.hibernate.Session;
import org.hibernate.Transaction;
import persistence.HibernateUtil; import org.dom4j.*;
public class DynamicMapping {
public static void main(String[] args) {
Session session = HibernateUtil.getSessionFactory().openSession().getSession(EntityMode.DOM4J);
Transaction tx = session.beginTransaction(); Query deleteQuery = session.createQuery("delete from Student");
deleteQuery.executeUpdate(); tx.commit(); tx = session.beginTransaction();
//create some some student and save them
{ Element anStudent = DocumentHelper.createElement("Student");
Element nameElement = DocumentHelper.createElement("name"); nameElement.setText("Alice");
Element lastNameElement = DocumentHelper.createElement("lastName"); lastNameElement.setText("Cooper");
anStudent.add(nameElement);
anStudent.add(lastNameElement);
session.save(anStudent);
}
{
Element anStudent = DocumentHelper.createElement("Student");
Element nameElement = DocumentHelper.createElement("name"); nameElement.setText("Lea"); Element lastNameElement = DocumentHelper.createElement("lastName");
lastNameElement.setText("Connor");
anStudent.add(nameElement); anStudent.add(lastNameElement);
session.save(anStudent);
}
tx.commit();
//List all student Query q = session.createQuery("from Student ");
List students = q.list(); org.dom4j.Element el = (org.dom4j.Element)students.get(0); System.out.println(el.getText());
for (Iterator it = students.iterator(); it.hasNext();)
{
org.dom4j.Element student = (org.dom4j.Element)it.next();
System.out.println("Printing an Student details: ");
for ( Iterator i = student.elementIterator(); i.hasNext(); )
{
Element element = (Element) i.next();
System.out.println( element.getName()+": "+ element.getText());
} }
//retrieve an student, update and save it
q = session.createQuery("from Student where name =:studentName "); q.setParameter("studentName", "Alice"); Element alice = (Element) q.uniqueResult(); alice.element("name").setText("No Alice any more");
tx=session.beginTransaction();
session.save(alice);
tx.commit(); session.close();
HibernateUtil.shutdown();
} }
In the begging we create a session with dom4j entity mode. so it will return Dom4J elements as our entities. in next two blocks i have create two students one is Alice Cooper and the other is John connor (what does this name remind you? ;-) . we simply ask our session to save them as we do for usual POJO mode. Session know what to do with dom4j elements as it is configured as a DOM4J session.
In Second block we query our table and retrieve all entities into a list, but this list is not a list of Student POJOs instead it is a list of DOM4J elements. so we need to do some XML processing when we want to extract our entity properties. you can learn more about DOM4J at Here .
Next step we retrieve a single row, edit and save it into our database, Its all simple DOM4J operation which you should use over some elements to manipulate your data.
Build file that i used contains two target that we will use during this project. first one is hbm2ddl which will create our database structure and the second one is run target which will execute our main class. it is not required to include build file here you can download the sample and check it yourself. make sure you look at readme file before digging into execution of application.
In next few days I will try to do a simple benchmark for some simple CRUD operation to have a basic clue about DOM4J entity mode in our environment.